The idea was simple.. find someone who CAN get broadband, and share that broadband out to me wirelessly. In reality this proved alot harder than it seemed as an idea... First of all, where I live is surrounded by trees and mountainous terrain - not very suitable for line of sight technology such as 802.11 wireless.
Step 1 was to find a location which could get broadband and that I could somehow have line of sight to.
Winter time was approaching and the evenings were getting shorter already - a solution had to be put in place before the winter arrived in order to keep me sane. After a number of tree climbing episodes accompanied with a telescope i eventually spotted a house on a remote hill who I thought I knew the owner of - this was a major strike of luck! After verfiying its physical location I attempted to drive to where I thought the house was to inspect if it was the house i thought it was. My treetop investigation was correct - this was a house of a friend of the family as luck would have it. Finally.. my antenna mounting spot was located:
The idea was put to the owner of the house would he mind a small dish to be mounted on the roof of his house - in exchange for free broadband. To my suprise he was open to the idea! At this point, I decided I would put the previously purchased Stella Doradus wifi mesh antennas to use...
Now a plan had to be formulated... there were a huge number of obstacles yet.. firstly I didn't even know if I could manage to obtain a solid connection between the two points. WiFi suffers huge losses over long runs of coax cable and the run from my house to the point in the tree where i could see the remote site was very long indeed.
The wireless network must be hassle free - i opted to go for linksys routers and run open source linux based software on them for maximum stability and flexibility when it comes to configuring the devices. I went ahead and purchased a WRT54G (€50).

After much research I discovered the only way to get this to work would be to mount the linksys WRT54G up on the tree, powering it and communicating with it using a single CAT5 cable. CAT5 cables contain 8 strands of wire. only 4 of these are used for data exchange, leaving the other 4 redundant. Using PoE (power-over-ethernet) these 4 unused wires can be used to carry power to the device.
From my old amatuer radio days I have a large radio mast, I decided to put this to some use and erect it in the tree, using the tree as support would mean relatively hassle free erecting of the mast and the need to tie the mast to the ground with metal wires wouldn't be as much of an issue. 4 sections of the mast, each 10 foot were erected over a period of two weeks. Many branches had to be cut away in order to allow the mast to be erected in a proper vertical manner. I almost died doing this at one stage when i fell halfway down the HUGE tree only to land on a branch before i hit the ground.
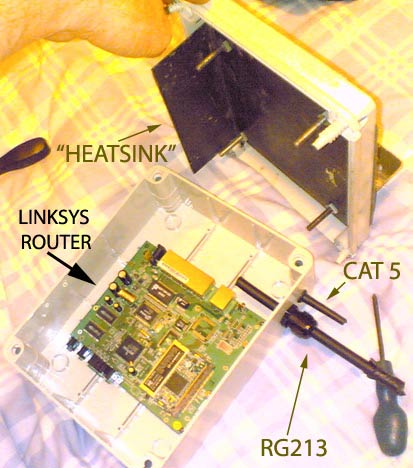
The next step was to mount the linksys up the tree on the mast - this thing needs to just work without problems. A trip to maplin resulted in discovering an outdoor waterproof project box to house the router in. Along with some waterproof grommets for the cable I was ready to go. The linksys was ripped apart leaving only the circuit board and this was put into the project box. Here's how it looked after the cabling holes were drilled:

The thick cable on the right is RG213 - very high grade coax for absolute minimal signal loss. This run of cable would be a max of 1 metre to the antenna which would be mounted above the box on the mast itself.

Since the linksys would be in a waterproof box cooling would be an issue, maybe not so much in the cold winter months but definitely when the summer time would arrive. In order to overcome this a metal heatsink was created from some spare metal, the metal was welded, drilled, sanded and then bolted onto the box.
Here's the external part of the heatsink... notice the "bracket" for securing the box to the mast:
My hope was the metal plate inside the box would absorb the heat coming from the transmitter and seep out thru the bolts onto the external metal plate.
With the mast in place the cat5 had to be run from the house... my initial cable was regular indoor cat5, I knew this would not be a permanent solution because it's such flimsy cable - after some initial pains with getting PoE to work the cable was scrapped and replaced with outdoor cat5 that a friend of mine had lying around. This cable was much better - it was still and had a very strong outer plastic layer.
Using some wiring diagrams i got off the internet and some old CAT5 socket boxes the power over ethernet system was constructed successfully.
The linksys is powered
by 18 volts to compensate for the power loss in the long run of PoE cat5. A test signal was successfully established without ANY problems - I knew I was now going to have a solid connection between the two endpoints. A smaller dish was mounted on the remote site's roof, and the router was installed and powered up.
I've always had my internet connection (dialup) shared using an old faithful freebsd machine ... I put another network card into this machine which I had lying around and configured a firewall and NAT to provide internet access to the machines on my LAN. BROADBAND HAD ARRIVED!
Thou it may not look it from the picture above.. the antenna is situated quite high off the
ground:
This elevation
offers direct line of sight to the house up the river at the other end of the
valley, here's a view from the bottom of the antenna on the
tree:
At the remote end
there's another LinkSys WAG54GS (a 3 in 1 device: wifi, ethernet and dsl modem) which is connected to another directional antenna. Unfortunately the WAG54GS came with a hardwired tiny plastic antenna since linksys did not imagine this device would be used for long range applications. In order to fit the antenna the WAG45GS had to undergo some surgery - the plastic antenna was removed, the coax desoldered and a new connection soldered onto the mainboard which i robbed from another WiFi router i'd lying around the place.
I encountered several annoying problems with the setup after a few days of use. The WAG54GS which was not capable of running the open source software was unstable and seemed to lock up after a few days of being switched on. This was no good and I had to repeatidly ask the owner to restart the stupid thing. I upgraded the firmware to a blistering edge copy i found on a beta firmware linksys site which according to linksys would solve the known problem with lockups in the earlier firmware.
No such luck - the device still started locking up. During these lockups the device was pingable, but could not be access via the web interface and it would not route any traffic.
A hack type solution had to be put inplace - I setup a cronjob which performed a HTTP POST on a nightly basis which rebooted the device. and 5 minutes later enabled "debug mode" which basically just enables a telnet daemon. More weeks passed and I eventually pinpointed a potential problem - a noticed a number of UPNP daemons running on the device which seemed to consume quite alot of its tiny memory space. I disabled UPNP - this seemed to help things!
The result of all this was that I now had a stable network.. my 3MB broadband still was not performing as good as it should.. this led to me experimenting with the wireless network settings.. eventually i found the magic combination - i disabled all "automatic" style settings and changed them to fixed settings. These settings when changed (e.g. Use MIXED [b/g] wifi technology changed to Use B technology, auto detect network speed was changed to a fixed 5.5MBps) resulted in a stable transfer speed.. where I used get up to 60KB was now bursting up to 210KB/s! A vast improvement. I also noticed a constant ping would show sporadic increases in network latency times... changing all these settings from auto to fixed values helped this anomaly too.
Finally, here's a picture of the finished product itself:
There you have it! I have broadband now and it was definitely worth all the hassle.